April 4, 2024
Nonprofit Technology & Fundraising Blog
Subscribe to our mailing list
April 1, 2024 | Categories DonorPerfect Fundraising Software, Featured, Nonprofit Technology, SofterWare Products
You have the privilege of serving your community through your mission. As a leader who serves others, you have countless donors who trust you with their money and their information. As such, it’s important for you to safeguard this revenue and their information by finding strategies that work for you and your team to ensure their security. So what kinds of steps can you take to make sure you are protecting your donors’ information and resources?
Internet threats and fraud schemes are real and innumerable. Bad actors can easily assail websites that are not properly safeguarded to collect sensitive data like credit card and bank account information. It is essential for you to take the necessary steps to make sure your donors’ payment information is safe. One simple way to do this is to sign up for a payment gateway service that is PCI compliant.
PCI (Payment card industry) compliance is a series of requirements established by major credit card companies to ensure the safety of data being processed, stored, or transferred through online solutions.
While using a PCI compliant gateway is not required by law, it garners your donors’ trust and makes it more likely that you will receive donations from tech-savvy supporters.
DonorPerfect’s in-house payment processing solution, SafeSave, offers low-cost transaction fees with no hidden costs, while still getting the high-tech security and PCI compliance offered by larger processors.
Electronic wallets, like PayPal, offer built-in security and protection for your donors. PayPal is a familiar platform for millions of people worldwide and a trusted payment processor. Look for an online forms product, like DonorPerfect’s donation forms, that will allow you to link your organization’s PayPal account and offer it as a payment option to your donors. PayPal even provides the opportunity to create monthly gifts that will continue to regularly process recurring payments.
Even government agencies with access to the best safeguards can be vulnerable to cyber-attacks. It’s important to guard against such attacks by setting policies in place that will protect your donors’ most sensitive information. With your staff, gather a list of information that should NOT be stored in your database. Discuss with your team if it is absolutely essential to keep data stored, and determine a time limit on how long you hold on to information that is vulnerable to attack.
Examples of data that should NOT be stored:
Some organizations have a lot of staff, volunteers, and board members accessing their database. While each individual may have a need to view information, most likely not all parties need to be granted permissions to all functionalities. After all, there are a lot of tools in a database that can make major and unexpected changes, and it’s important that only those who are more well-versed in the database be given permissions.
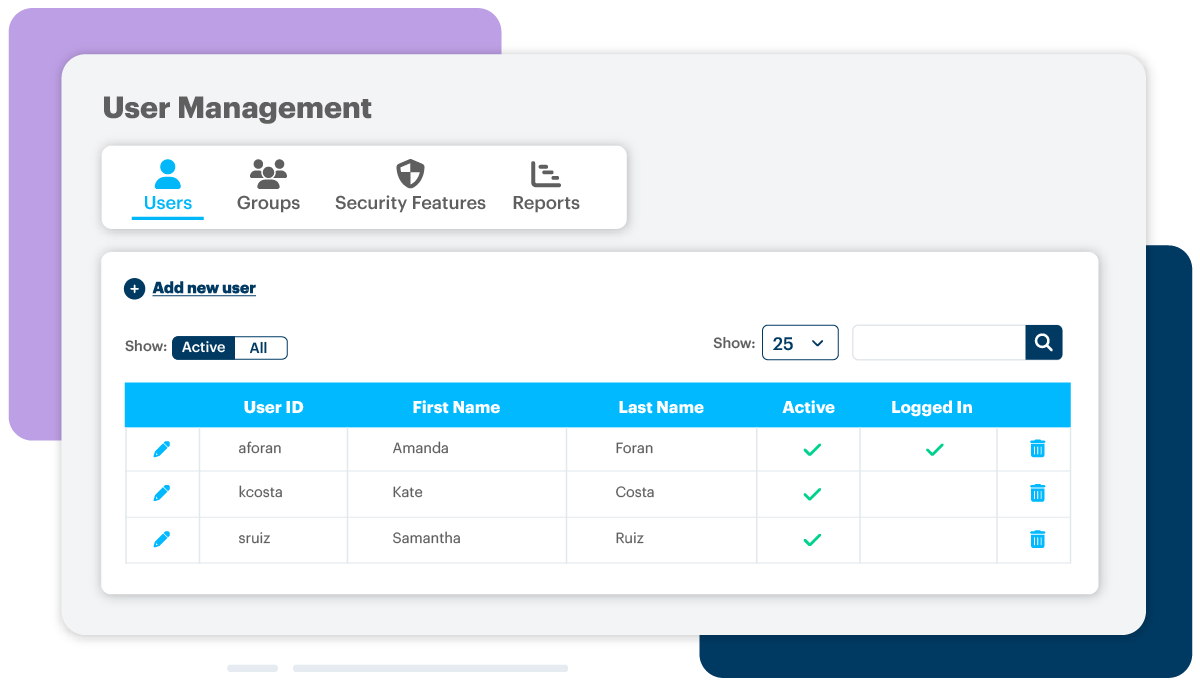
In DonorPerfect, you can restrict access in a number of ways:
In addition to setting certain limits on access, it is also important to remove permissions entirely when an individual is no longer serving your organization. In order for these limits to work, it is also essential that those using your database not share a username. Each person logging in should be doing so with their own credentials. Make sure the right people at your organization know how to create users, set permissions, and deactivate or remove access.
DonorPerfect offers unlimited user IDs with security features like user groups to make setting and managing permissions easy.
A lot of software products offer security features, but it is up to the user to set them up and use them. These features could be options like setting expiration dates on passwords, setting requirements to ensure passwords are complex enough, and connecting IP addresses to logins.
As an additional security measure, you can set a protocol for passwords to be changed at a certain frequency. Changing passwords often will help to keep your database safe from intruders, and will disable access to anyone who may have infiltrated with a previously created password.
DonorPerfect allows you to set expiration dates on passwords. An admin user can select the length of time after which a password will expire. Then, the system will automatically force a user to change their password before logging in again.
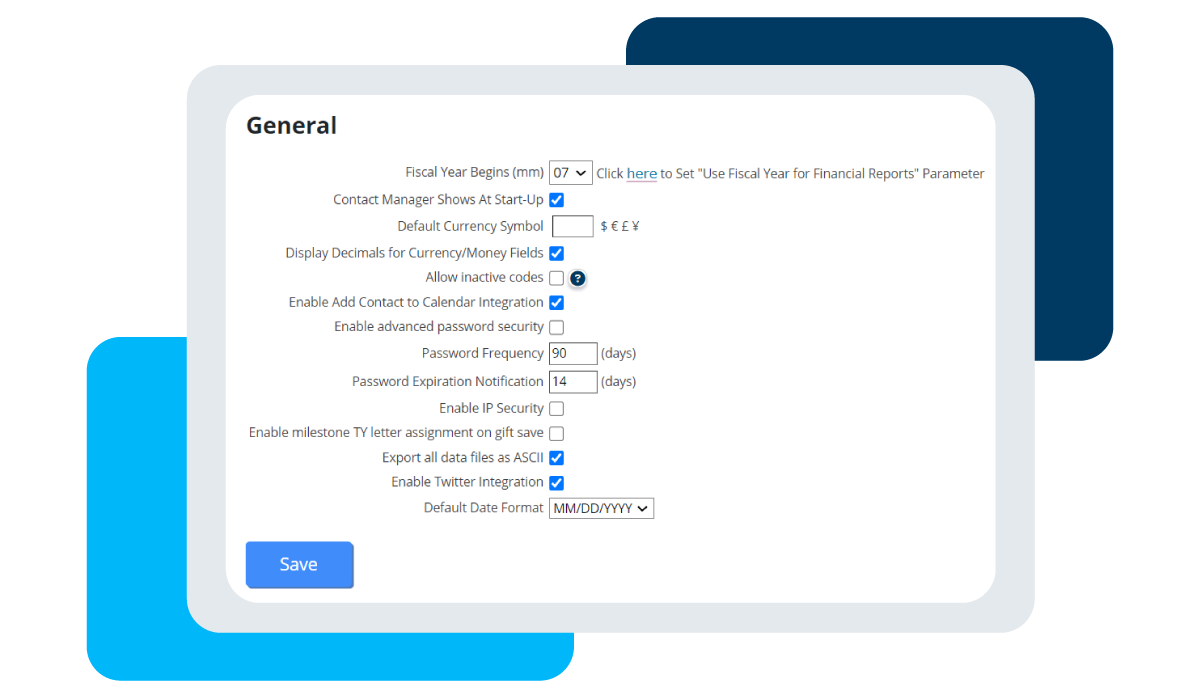
Password requirements help ensure the complexity of passwords, making it hard for a person’s credentials to be guessed. Requirements could include things like upper and lower case characters, special characters like a dollar sign or an asterisk, and a minimum length of characters. DonorPerfect passwords require at least nine characters as well as at least three special characters and upper and lower case letters.
Setting restrictions on the IP addresses accessing your database is another excellent tool you can use to protect your database. An IP address is not a physical address, but rather a numerical label assigned to a device that is connected to a computer network. Some softwares, like DonorPerfect, allow you to define what IP addresses can be used to log in to your database. This provides an additional layer of security for any users who may have gained access to your passwords but are not using an IP address with permissions.
Reconciliation is an essential task in ensuring no data entry errors have been made and funds are where they need to be. It’s a good idea to have a regular schedule for how often and who should be in charge of reconciliation. If you have the bandwidth, it is even advisable to have multiple people perform separate, but matching reconciliations to create a set of checks and balances among your team. If you work with multiple databases, you may want to perform cross-reconciliation as well.
Establishing procedures for your organization may not be at the forefront of your mind when you have countless fundraising tasks to attend to, but it is essential to keeping your donors’ data safe and your organization thriving. Once procedures and policies are in place, they work to keep your nonprofit running smoothly, especially during difficult or transitional times.
When it comes to creating a policy guide, DonorPerfect can help. Download our Clean Data Checklist for help on everything from data entry procedures to keeping your most sensitive information safe and secure.